If a website isn't working or down, it may happen due to malicious scripts activity.
In order to solve the problem with malicious inserts and scripts, follow an instruction (from simple to more complex):
- Check website online https://sitecheck.sucuri.net/.
This check may point out a problem.
- If an additional software (plugins / themes) was recently installed on a website, make sure that the source of this software is reliable.
- Make sure that all plugins and themes that are currently used on the site are not compromised and don't contain any critical vulnerabilities.
- Make a list of all your plugins.
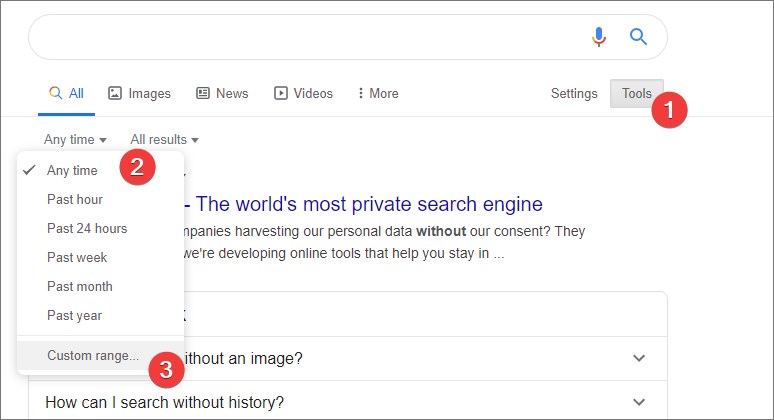
- Go to Google search -> Tools -> search by last 3 months.
- Search string "plugin_name critical vulnerability"
It will help you define if there were critical vulnerabilities that may lead for many websites hacked.
This quick check may lead you to a vulnerability in the plugin.
- Log into database phpmyadmin or to the website control panel. Check the number of users, especially with administrator privileges. If there are suspicious users, delete them.
- Remove all files from the website root catalog and drop database.
Restore the website from a backup. Change passwords: to hosting private area, to the website's control panel, to the database (you will need to reconfigure the database connection in code).
- Install security plugin. For wordpress install iThemes Security plugin and configure it.
- Parse website access log for POST queries.
- Contact hosting company and ask for a help in cleaning up viruses and closing the vulnerabilities. This will most likely be a paid service.
- Check website for viruses and clean it.
Use ai-bolit utility from revisium.
Download ai-bolit and run the test. Example:
php /root/aibolit/ai-bolit.php \
--size=900K \
--mode=2 \
--path=/var/www/directory_before_website/your_website/ \
--report=/var/www/directory_before_website/your_website/vir.html \
Malicious scripts can also be located outside of the website's root catalog,so checking the directory above is a good idea. Change the --path key:
--path = /var/www/directory_before_website/
You can open the report by the link:
https://your_site.ru/vir.html
Using the report, go through and clean the site of malicious inserts.
- Clean the database from malicious inserts.
- Manually check website for malicious code and vulnerabilities.
- After cleaning the site of viruses, configure antishell script.
Antishell script checks website for any changes in code and sends email with the report if any changes have been done. Using antishell it is possible to know the time of an injection and what scripts were hacked. Having the conrete time, its possible to parse through access log and find the IP and queries to website.





